Why Topos?
In a nutshell, Topos brings ease of deployment, uniform security, scalability and provable computation to cross-chain transactions.
In the rapidly evolving world of blockchain technology, the importance of scalability, security and efficiency cannot be overstated. As developers and businesses explore the potential of decentralized applications (dApps), they seek a platform that can deliver on these fronts. This is where Topos stands out. With its advanced approach to blockchain architecture, the Topos ecosystem addresses the critical challenges faced by other blockchain platforms. It offers:
- High blockspace supply
- Robust security measures
High blockspace supply
Topos provides an impressive degree of scalability. It can handle substantial computational loads without compromising performance, which provides an efficient mechanism to create and broadcast certificates.
Robust security measures
The safety of the Topos ecosystem is independent of the security of the participating blockchains (called subnets). It is computationally infeasible for malicious subnets to create invalid state transitions or to create conflicting states in order to double spend across the ecosystem.
In the sections that follow, you will delve into these aspects in more detail to gain a comprehensive understanding of what makes Topos a unique and powerful choice on which to develop and host dApps.
Computing power
Topos is designed with a unique architecture that alleviates computational bottlenecks in two major ways. Firstly, it allows for boundless horizontal scalability, through the use of a passive and lightweight settlement layer that supports multiple connected subnets. Secondly, it enables computation compression through the use of validity proofs, which replaces costly re-execution with succinct verification.
Advanced security
Topos was designed to serve as the base layer of the internet by reducing trust assumptions in involved parties as much as possible and replacing them with cryptographic constructions and decentralization. Alongside this, Topos is engineered to exhibit massive scalability, envisioning a future where these attributes become the norm for online infrastructures.
Certificates for secure communication
In Topos, certificates play a crucial role in ensuring secure and reliable communication between different subnets. A certificate is a data package that proves the validity of a sequence of transactions.
A certificate is created by a source subnet, sent to the TCE, and then onwards to a list of target subnets. Certificates allow target subnets to safely execute cross-subnet messages.
Certificates do not contain any of the transactions that are proven by the validity proof. Certificates only contain the validity proof as well as the metadata necessary to verify the proof.
The Topos protocol effectively addresses the security risks inherent in cross-chain technology, providing a high level of privacy and security for applications. For developers, this means they can build secure and natively interoperable dApps.
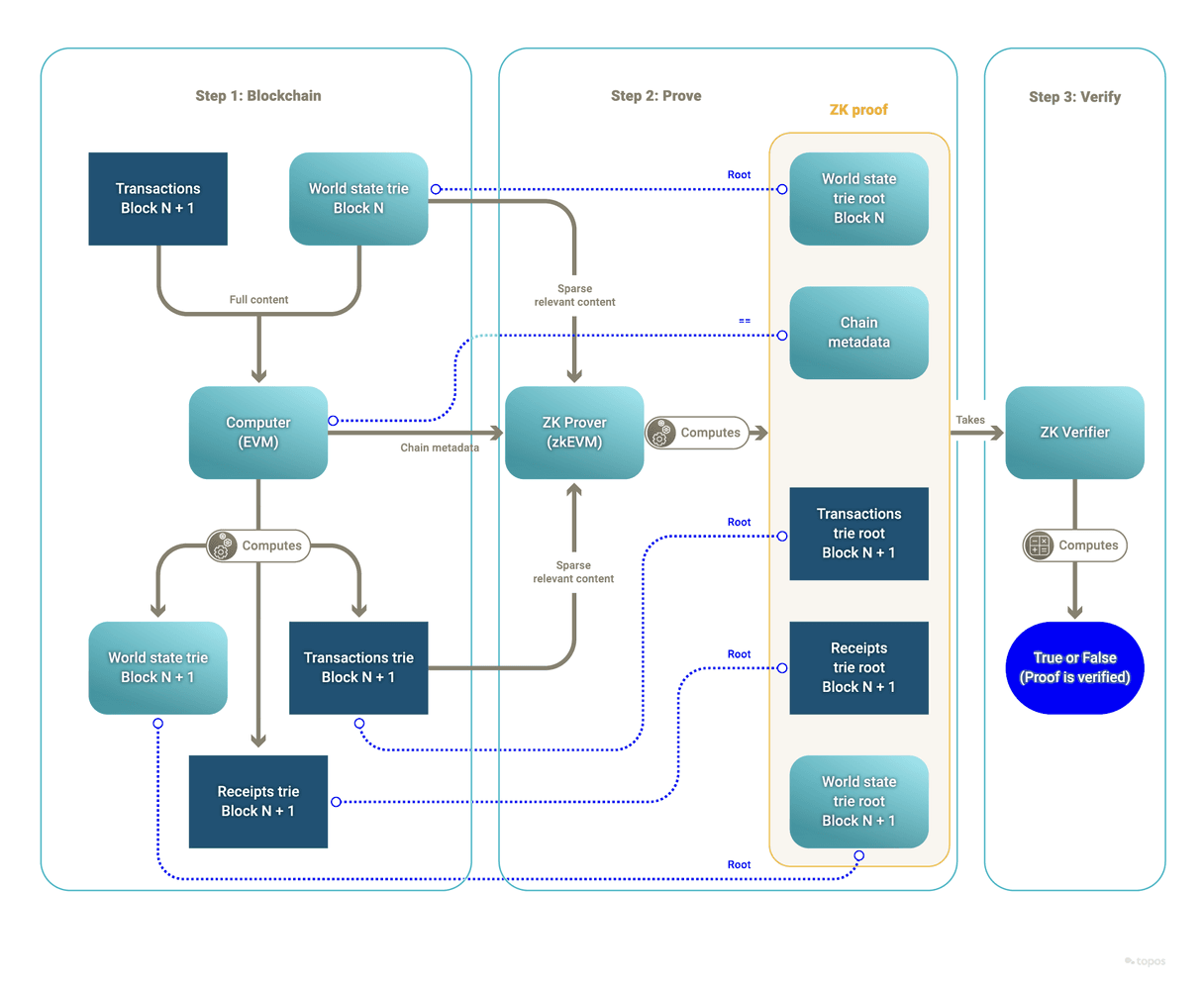
Privacy through zero-knowledge proofs (ZKPs)
ZKPs in general
ZKPs are a form of cryptographic method that allow one party to prove to another party that they know specific information, without revealing any private information. Certain variants of ZKPs are used to prove that a potentially complex computation was performed, with the verification of the ZKPs taking significantly less time than the initial computation. These methods enable privacy without adding any significant computation burden.
ZKPs with Topos
In the context of Topos, ZKPs are used to prove that transactions have been validated and their outcomes computed according to the protocol while keeping sensitive transaction details hidden. This technology represents a significant advancement in maintaining user privacy while retaining the ability to transparently verify the transaction history.
Up next
In the next section, you will explore an overview of some use cases for Topos technology.